Dec 30, 2008
How to fix DNSChanger Malware
The trojan modify some registry at TcpIp service and maybe it also adds some Windows service for monitoring...
To fix it
Option 1. Disable the DNS Client service (the service has no effect on client machine, it normally cache the DNS request to optimize)
Option 2. Download the CombFix http://download.bleepingcomputer.com/sUBs/ComboFix.exe and run, it'll automatically fix the issue for you.
Dec 29, 2008
Dec 23, 2008
Holiday Calendar in Outlook for Vietnam company
1. Create a file with extension .HOL (i.e. outlook.hol) with following contents
[GCS] 102. Double click on the file to import the holiday list into Outlook, just do it one time.
New Year's Day,2009/1/1
Independence Day,2009/4/30
Christmas Day,2009/12/25
International Labor Day,2009/5/1
National Day,2009/9/2
Lunar New Year Eve,2009/1/25
Lunar New Year Day 1,2009/1/26
Lunar New Year Day 2,2009/1/27
Lunar New Year Day 3,2009/1/28
Hung Kings Commemorative Holiday,2009/4/4
Have fun.
A day in a park
1 ngày trong sở thú của tui, có rất là nhiều điều kỳ thú. Sau 1 ngày lặn lội săn tìm nhưng đĩa mồi cho bàn nhậu
1. Da cá sấu nướng trui

2. Chồn hương bóp thấu

3. Sườn tê giác muối chiên giòn

4. Chúa sơn lâm thui

5. Khỉ nướng trui + óc khỉ

6. Giò voi chiên nước mắm

7. Mật gấu

Và cái món cuối cùng vô cùng đặc biệt.
8. Binbui lột da cháy tỏi

Trong lúc chờ đợi các quán nhậu cập nhật danh sách những món trên thì trong lúc đó tui làm đại cái con gà cho đỡ thèm ![]()


Và không quên bánh mì nữa chứ

Heheh, have fun ![]() (the image is from GCS Christmas Night 2008, more to come)
(the image is from GCS Christmas Night 2008, more to come)
Nov 29, 2008
Nov 17, 2008
Nov 16, 2008
Turn off display non-secure item popup dialog in Internet Explorer
Step 2: Select the "Security" Tab and then click on the "Custom Level" button
Step 3: Scroll down until you see the option: "Display mixed content". Sect the option "Enable" (in the Miscellaneous section)
Step 4: Click Ok
Enable exFAT in Windows XP/2003
Create the following registry file "enable-exfat.reg"
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\exfat]
"Description"="exFAT File System Driver"
"DisplayName"="exFAT File System Driver"
"ErrorControl"=dword:00000001
"Group"="Boot File System"
"Start"=dword:00000002
"Type"=dword:00000002
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\System\exfat]
"EventMessageFile"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,\
00,6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,\
5c,00,49,00,6f,00,4c,00,6f,00,67,00,4d,00,73,00,67,00,2e,00,64,00,6c,00,6c,\
00,00,00
"TypesSupported"=dword:00000007
Run the file to import it into registry.
Restart your PC and the exFAT will be enabled
Cheers,
-Hieu
Nov 12, 2008
BarCamp event at Ho Chi Minh city
This event is free and all GCS employee are welcome to join, just go to http://barcampsaigon.org/ to register yourself.
Global CyberSoft is also a gold sponsor for this event :-)
The following is the list of session in the BarCamp.
- Offered Sessions
- 30-minute sessions
- Teaching programming with Alice [En] – Huy Zing
- Vietnam web services portal & Start-ups Support System| Cổng thông tin về dịch vụ Web ở Việt Nam & Hệ thống hỗ trợ start-ups[EN & Vi] – Huyền Chip
- How to quickly create a web form with Google Docs [En & Vi] – Huyền Chip & Huy Zing
- E-learner Platform 2.0 [En & Vi] – Anh Hùng
- GIS-related session (topic is not decided yet) [En & Vi] – Khánh Lê
- Interesting Web/Mobile Projects in Asia and Africa and how they are being monetized. [En] (with Vn subtitles) Preetam Rai
- Intel and Intel Vietnam company presentation and job opportunities. Huan Duong
- Cloudworking and Monetizing Models and life style of a mobile CEO/entrepreneur. Dan Lilly & Tom Tran
- Giới thiệu cuộc thi “Search for ASEAN XML SuperStar” [Vi] – Khiem, IBM VN
- Giới thiệu quy trình phát triển phần mềm RUP [Vi] – Minh, IBM VN
- 1-hour sessions
- Google App Engine app development [Vi & En] – Loi & Huy Zing
- Android app development [Vi & En] – Tuan & Huy Zing
- Adobe AIR development [Vi & En] – Justin & Huy Zing
- iPhone app development [Vi & En] – Multinc
- Essential Ingredients of a Successful Web Business [En] - Chris Harvey
- Ventures Capital Tips: Getting funded and Operating a start-up [Vi & En] – James Vuong & Hiep Do IDGVV
- 30-minute sessions
- Requested Sessions
- Using Ruby/JRuby (or Python/Jython) for scripting/sysadmin and GUI applications, on Windows.
- Developing some Extensions,Plugins,Themes for Mozilla Firefox , on Windows.
- Start-ups, Entrepreneurship, and Business Development: Owning your own business in a global economy
Nov 11, 2008
Remove xxx activation in yyy 2008
Nov 2, 2008
PDC 2008 Session Video
Have fun
Nov 1, 2008
How to unlock attachment restriction in Microsoft Outlook
- Start => Run => Enter regedit
- Look for HKEY_CURRENT_USER\ Software\ Microsoft\ Office\ 10.0\ Outlook\ Security
- Create a new String value Level1Remove (modify if exists) and add the extension that you would like to allow for download (seperated by comma) ex: exe;jpg;gif;png
Note: These are the list of files that is normally being lock by Ms Outlook when received as e-mail attachments: “ade, adp, asx, bas, bat, chm, cmd, com, cpl, crt, exe, hlp, hta, inf, ins, isp, js, jse, lnk, mda, mdb, mde, mdz, msc, msi, msp, mst, pcd, pif, prf, reg, scf, scr, sct, shb, shs, url, vb, vbe, vbs, wsc, wsf, wsh”
Oct 27, 2008
Oct 26, 2008
Top Technology Trends for 2009
These are Top Technology Trends for 2009
- Virtualization
- Cloud computing
- Servers
- Web-oriented architectures
- Enterprise mashups
- Specialized systems
- Social software and social networking
- Unified communications
- Business intelligence
- Green IT
What do you think? :-)
Oct 23, 2008
How to Disable Steal Lock in Subversion
pre-lock.bat
The following is the content of pre-lock.bat which will work on Windows environment. Just copy the content and put it under the hook folder of your Subversion repository
@ECHO OFF
:: Set all parameters. Even though most are not used, in case you want to add
:: changes that allow, for example, editing of the author or addition of log messages.
set repository=%1
set rev_path=%2
set userName=%3
:: If a lock exists and is owned by a different person, don't allow it
:: to be stolen (e.g., with 'svn lock --force ...').
FOR /F "delims=: tokens=1*" %%a IN ('svnlook lock "%repository%" "%rev_path%"') DO if %%a==Owner (set LOCK_OWNER=%%b)
:: If we get no result from svnlook, there's no lock, allow the lock to
:: happen:
if "%LOCK_OWNER%"=="" (
exit /b 0
)
:: If the person locking matches the lock's owner, allow the lock to
:: happen:
if "%LOCK_OWNER%" = " %username%" (
exit /b 0
)
:: Otherwise, we've got an owner mismatch, so return failure:
echo "Error: %rev_path% already locked by %LOCK_OWNER%." >&2
exit /b 1
Enable Edit Log Message in Subversion
To enable it to user, you (the SVN admin) must enable the pre-prop-change hook
pre-prop-change.bat (Windows)
Here is the content of pre-prop-change hook, just save it to pre-prop-change.bat and copy it into SVN hook folder. The content is Windows batch file and just for Windows environment
The script will enable the owner of the revision and the owner of SVN to change the log message.
The owner of SVN is get from SVN auth file (authz-svn.conf) and should be configure in the form @svn_owner = userA, userB...
You need to edit the PATH to authz-svn.conf file
@ECHO OFF
:: Set all parameters. Even though most are not used, in case you want to add
:: changes that allow, for example, editing of the author or addition of log messages.
set repository=%1
set revision=%2
set userName=%3
set propertyName=%4
set action=%5
:: Only allow the log message to be changed, but not author, etc.
if /I not "%propertyName%" == "svn:log" goto ERROR_PROPNAME
:: Only allow modification of a log message, not addition or deletion.
if /I not "%action%" == "M" goto ERROR_ACTION
:: Make sure that the new svn:log message is not empty.
set bIsEmpty=true
for /f "tokens=*" %%g in ('find /V ""') do (
set bIsEmpty=false
)
if "%bIsEmpty%" == "true" goto ERROR_EMPTY
FOR /F "tokens=*" %%a IN ('svnlook author "%repository%" -r %revision%') DO set REV_USER=%%a
FOR /F "delims== tokens=1*" %%a IN (%repository%\..\Permission\authz-svn.conf) DO if "%%a"=="svn_owner " ( set SVN_OWNER=%%b )
set bIsOK=false
FOR %%a IN (%SVN_OWNER%) DO if "%%a"=="%userName%" ( set bIsOK=true )
if "%bIsOK%"=="false" (
goto ERROR_AUTHOR
)
goto :eof
:ERROR_AUTHOR
echo You must be the author of the log message or owner of the repository %SVN_OWNER% %userName%. >&2
goto ERROR_EXIT
:ERROR_EMPTY
echo Empty svn:log messages are not allowed. >&2
goto ERROR_EXIT
:ERROR_PROPNAME
echo Only changes to svn:log messages are allowed. >&2
goto ERROR_EXIT
:ERROR_ACTION
echo Only modifications to svn:log revision properties are allowed. >&2
goto ERROR_EXIT
:ERROR_EXIT
exit /b 1
pre-prop-change (Linux)
The following is the script in Linux, it just allow the owner of the revision to change the log.
#!/bin/sh
REPOS="$1"
REV="$2"
USER="$3"
PROPNAME="$4"
ACTION="$5"
if [ "$ACTION" = "M" -a "$PROPNAME" = "svn:log" ];
then
REV_USER=`svnlook author "$REPOS" -r $REV`
if [ "$REV_USER" = "$USER" ];
then
exit 0;
else
echo "You must be the owner of the revision to be able to change the svn:log property" >&2
exit 1
fi
fi
echo "Changing revision properties other than svn:log is prohibited" >&2
exit 1
Oct 16, 2008
StyleCop command line
Here is a version of StyleCop in command line mode - http://www.nichesoftware.co.nz/content/stylecop-cmd. You need to have VS 2008 in order to compile, or you can install .NET 3.5 and compile using MSbuild command
set PATH=%PATH%;C:\WINDOWS\Microsoft.NET\Framework\v3.5
cd C:\StyleCopCmd-1.1.27.5997\src\StyleCop
msbuild StyleCop.csproj
Oct 15, 2008
How to copy music from PC to iPhone without using iTunes
Hehe, you will need to use the SharePod at http://www.getsharepod.com/ and everything will be solved ;-)
Oct 13, 2008
Some funny VNese translation in Google

Dịch thế này thì... bó tay.

Miễn bàn.

Google Translate chọn từ rất "đắt".

Đời rất... tí.

Với Google, ngoại tình là "tư tưởng ngoại".

Google không hiểu "tình" là gì?

Enjoy the afternoon cũng giống như cách dịch "like is afternoon".

Google không dịch từ "ruồi", còn "mật" tương đương với "chính sách".

...

Tôi too khờ!!!

Sep 20, 2008
Disable Certificate Error Report in IE7
This does not indicate a problem with the website or control panel. This could be more acurately described as a fault with Internet Explorer being a little overly paranoid on your behalf.
Your choice is to either click that you want to navigate the site anyhow, or permanently disable the warning.
If you would like to permanently disable the warning error, go to the Internet Explorer Tools menu and select Internet Options, Advanced tab. Scroll down to the bottom (under Security) and disable/uncheck "Warn about certificate address mismatch".
Sep 8, 2008
Knowledge Sharing in Software Development
I know some of you tend to resist sharing your knowledge with the rest of the organization, some of you don’t know what to write, it’s because of the system and blah blah blah. Just stop blaming on the system, we should change our mindset and our behavior in using the tools.
Here is some practices for sharing
- Knowledge is from project.
- Each project must have trouble, issue, development tips & tricks, environment setup, this is the knowledge – (as I have seen in some projects, the development environment is kept inside developer’s mind, when newcomer come to the project, at least 1 dev will sit with him for setting up the environment)
- We’re not master, but when facing the problem we should be, this is where knowledge come from.
- You’re in the project so it definitely that you’ll have some knowledge to share otherwise you look like a “chess man” in project.
Will you try out the Wiki? Some wiki you might be interested in
- http://www.twiki.org/
- http://www.mediawiki.org/wiki/MediaWiki
- Microsoft SharePoint Server
Aug 20, 2008
What is Twitter?
You can't really understand Twitter unless you actually do it (which might explain why I don't really understand Twitter.)
The benefit of Twitter is "social proprioception":
When I see that my friend Misha is "waiting at Genius Bar to send my MacBook to the shop," that's not much information. But when I get such granular updates every day for a month, I know a lot more about her. And when my four closest friends and worldmates send me dozens of updates a week for five months, I begin to develop an almost telepathic awareness of the people most important to me.
It's like proprioception, your body's ability to know where your limbs are. That subliminal sense of orientation is crucial for coordination: It keeps you from accidentally bumping into objects, and it makes possible amazing feats of balance and dexterity.
Twitter and other constant-contact media create social proprioception. They give a group of people a sense of itself, making possible weird, fascinating feats of coordination."
Sound interesting? It should have more :-)
Aug 3, 2008
Aug 1, 2008
How To Compile C Code Analysis (CCA)
Prerequisite
- Cygwin: gcc, ocaml, make
cd cilYou might need to edit the Makefile.cil to remove the following lines (at line 259)
./configure
make
make quicktest
$(ECHO)#if test $(OBJDIR) != $(<D) -a -f $(OBJDIR)/$(basename $(<F)).cmi ;then \
$(COMMAND) mv -f $(OBJDIR)/$(basename $(<F)).cmi $(<D); \
mv -f $(OBJDIR)/$(basename $(<F)).cmi $(<D); \
fi
Jul 27, 2008
How To Create DirectX (.X) file
- Get yourself a program named TrueSpace or Milkshape, which can export Models into this format (and create them)
- Get a Plug in for any other 3D modeler (Maya Plugin and others are included with the DirectX9 SDK)
- Create 3DS Files using almost Any Modeler (3DS is more or less a standard format) and use the Program supplied with the SDK to convert it into .X format
- Open the File in WordPad and u can create/modify them, since they are not stored in any compressed/unreadable format (although for this u need to know how the file is build)
- Create the mesh
D3DXCreateMeshFVF(...)
- Lock the vertex buffer and copy your vertices into it
outMesh->LockVertexBuffer(...)
- Lock the index bufer and copy indices into it
outMesh->LockIndexBuffer(...)
- Save it to a file
D3DXSaveMeshToX(...)
Jul 19, 2008
Collaborative Development Environment at GCS
Today, we use many tools to support the collaboration such as email, instant messaging, chat rooms, discussion groups, and Wikis… Collaboration among teams is already facilitated through the use of an increasing number of features embedded in standard desktop products such as office suites, where there is ample support for shared document reviews, distribution of documents among teams, and mechanisms for performing common collaborative tasks. In a very practical sense these tools provide the baseline of collaboration functionality for today’s software developers.
At Global CyberSoft (GCS) we have CDE and more than CDE, it is Collaborative Development and Management Environment (CDME) hehehe
Jul 16, 2008
Best Practices for Software Development
1. Development process - It is important to choose the appropriate development lifecycle process to the project at hand because all other activities are derived from the process. For most modern software development projects, some kind of spiral-based methodology is used over a waterfall process. There are several choices, including the Rational Unified Process (RUP), IBM® Global Services Method, and eXtreme Programming (XP). Having a process is better than not having one at all, and in many cases it is less important on what process is used than how well it is executed. The commonly used methodologies listed above all contain guidance about how to execute the process and templates for artifacts. In addition, the RUP has a series of books that describe the best practices for using RUP [1][2][3][4] although if you do not choose to use RUP, these books still provide an excellent source of best practices. It is also possible to add plugins to the RUP. For a list of available plug-ins, see Plug-in Central.
2. Requirements - Gathering and agreeing on requirements is fundamental to a successful project. This does not necessarily imply that all requirements need to be fixed before any architecture, design, and coding are done, but it is important for the development team to understand what needs to be built. Quality requirements are broken up into two kinds: functional and non-functional. A good way to document functional requirements is using Use Cases. Note that Use Cases are used for non-OO projects. A definitive book on the subject of use cases is by Armour and Miller [5]. Non-functional requirements describe the performance and system characteristics of the application. It is important to gather them because they have a major impact on the application architecture, design, and performance. See the non-functional requirements checklist on the Construx Web site.
3. Architecture - Choosing the appropriate architecture for your application is key. Many times IBM is asked to review a project in trouble and we have found that the development team did not apply well-known industry architecture best practices. A good way to avoid this type of problem is to contact IBM. Our consultants can work side by side with your team and ensure that the projects get started on the right track. Tried and true practices are called patterns and they range from the classic Gang of Four [6] patterns, Java patterns [7], to EJB design patterns [8]. Sun's equivalent is the Core J2EE Patterns catalog [9]. Many projects fail as discussed in the introduction. The study of these failures has given rise to the concept of antipatterns. They are valuable because they provide useful knowledge of what does not work, and why.
4. Design - Even with a good architecture it is still possible to have a bad design. Many applications are either over-designed or under-designed. The two basic principles here are "Keep it Simple" and information hiding. For many projects, it is important to perform Object-Oriented Analysis and Design using UML. There are many books on UML, but we recommend UML User Guide [11] and Applying UML and Patterns [12]. Reuse is one of the great promises of OO, but it is often unrealized because of the additional effort required to create reusable assets. Code reuse is but one form of reuse and there are other kinds of reuse that can provide better productivity gains.
5. WebSphere application design - IBM has extensive knowledge of the best practices and design patterns for the WebSphere product family. Each project is different and our consultants have the experience to help you. There is still a tremendous return on investment (ROI) even if you only use the consultants for a short time because you save the costs later in the project. Our experts have also published a great deal of this wisdom, including considerations for high-performance Web sites and guidelines for autonomic computing.
6. Construction of the code - Construction of the code is a fraction of the total project effort, but it is often the most visible. Other work equally important includes requirements, architecture, analysis, design, and test. In projects with no development process (so-called "code and fix"), these tasks are also happening, but under the guise of programming. A best practice for constructing code includes the daily build and smoke test. Martin Fowler goes one step further and suggests continuous integration that also integrates the concept of unit tests and self-testing code. Note that even though continuous integration and unit tests have gained popularity through XP, you can use these best practices on all types of projects. I recommend using standard frameworks to automate builds and testing, such as Ant and JUnit.
7. Peer reviews - It is important to review other people's work. Experience has shown that problems are eliminated earlier this way and reviews are as effective or even more effective than testing. Any artifact from the development process is reviewed, including plans, requirements, architecture, design, code, and test cases. Karl Wiegers paper on the Seven Deadly Sins of Software Reviews explains the correct ways to perform peer reviews. Peer reviews are helpful in trying to produce software quality at top speed.
8. Testing - Testing is not an afterthought or cutback when the schedule gets tight. It is an integral part of software development that needs to be planned. It is also important that testing is done proactively; meaning that test cases are planned before coding starts, and test cases are developed while the application is being designed and coded. There are also a number of testing patterns that have been developed.
9. Performance testing - Testing is usually the last resort to catch application defects. It is labor intensive and usually only catches coding defects. Architecture and design defects may be missed. One method to catch some architectural defects is to simulate load testing on the application before it is deployed and to deal with performance issues before they become problems.
10. Configuration management - Configuration management involves knowing the state of all artifacts that make up your system or project, managing the state of those artifacts, and releasing distinct versions of a system. There is more to configuration management than just source control systems, such as Rational Clearcase. There are also best practices and patterns [13] for configuration management.
11. Quality and defects management - It is important to establish quality priorities and release criteria for the project so that a plan is constructed to help the team achieve quality software. As the project is coded and tested, the defect arrival and fix rate can help measure the maturity of the code. It is important that a defect tracking system is used that is linked to the source control management system. For example, projects using Rational ClearCase may also use Rational ClearQuest. By using defect tracking, it is possible to gauge when a project is ready to release.
12. Deployment - Deployment is the final stage of releasing an application for users. If you get this far in your project - congratulations! However, there are still things that can go wrong. You need to plan for deployment and you can use a deployment checklist on the Construx Web site.
13. System operations and support - Without the operations department, you cannot deploy and support a new application. The support area is a vital factor to respond and resolve user problems. To ease the flow of problems, the support problem database is hooked into the application defect tracking system.
14. Data migration - Most applications are not brand new, but are enhancements or rewrites of existing applications. Data migration from the existing data sources is usually a major project by itself. This is not a project for your junior programmers. It is as important as the new application. Usually the new application has better business rules and expects higher quality data. Improving the quality of data is a complex subject outside the scope of this article.
15. Project management - Project management is key to a successful project. Many of the other best practice areas described in this article are related to project management and a good project manager is already aware of the existence of these best practices. Our recommended bible for project management is Rapid Development by Steve McConnell [14]. Given the number of other checklists and tip sheets for project management, it is surprising how many project managers are not aware of them and do not apply lessons learned from previous projects, such as: "if you fail to plan, you plan to fail." One way to manage a difficult project is through timeboxing.
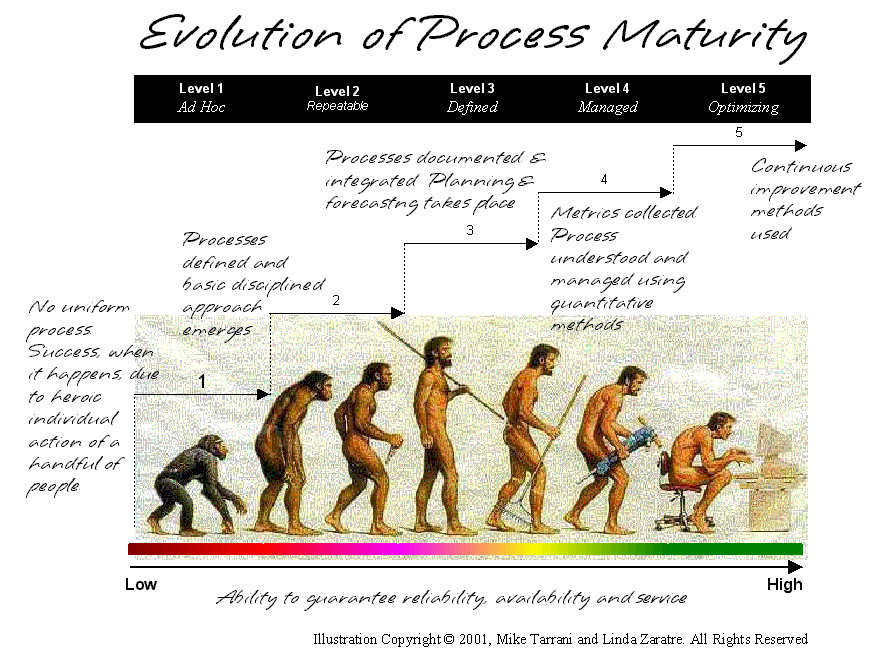
16. Measuring success - You can measure your development process against an industry standard known as the Capability Maturity Model (CMM) from the Software Engineering Institute at Carnegie Mellon University. Most projects are at level 1 (initial). If you implement the best practices described above and the guidelines in the companion article, Guide to Running Software Development Projects, then you could be well on the way to achieving a higher maturity level and a successful project.
Jul 10, 2008
Turn off Secure Connection Failed in Firefox 3
Secure Connection Failed
Hostname uses an invalid security certificate.
The certificate is only valid for *example.org
(Error code: ssl_error_bad_cert_domain)
Firefox 3 produces this error a lot for me. And I really hate it.
in about:config set:
browser.ssl_override_behavior = 2
This will fetch the cert (rather than asking to click to download it which is stupid - if you want it it means two clicks, if you don’t then cancel - besides, surely it’s downloaded the certificate already since it says it is insecure!)
browser.xul.error_pages.expert_bad_cert = true
display alert rather than staying on the previous page
Jul 7, 2008
T-Shirt for Hudson



More can be found here http://www.cafepress.com/hudson_ci/
Jul 3, 2008
Internship program at Global CyberSoft 2008
Here is the schedule
-Day 1: Company Structure, Division Introduction, CP4…
-Day 2: Introduction to SDLC, ISO, CMMI…
-Day 3: Microsoft Office SharePoint Server 2007
-Day 4: iPhone Application Development
-Day 5: Web 2.0 & RIA
-Day 6: Digital Signal Processing
-Day 7: Game Development
-Day 8: Open Discussion
Jun 22, 2008
Link for technologies (2)
Link for technologies (2)
Cai nay la ve OpenUP va EPF ne, doc mai~ moi understand duoc, thi ra no simple den the, lost about 1 year hic
- http://www.ibm.com/developerworks/rational/library/sep07/kroll/index.html?ca=...
- http://www.eclipse.org/epf/general/getting_started.php
- http://www.eclipse.org/epf/downloads/tool/tool_downloads.php
- http://www.eclipse.org/epf/downloads/praclib/praclib_downloads.php
- http://www.eclipse.org/epf/downloads/openup/openup_downloads.php
- http://www.eclipse.org/epf/downloads/xp/xp_downloads.php
- http://www.eclipse.org/epf/downloads/scrum/scrum_downloads.php
- http://www.eclipse.org/downloads/download.php?file=/technology/epf/PracticesL...
- http://www.eclipse.org/downloads/download.php?file=/technology/epf/PracticesL...
- http://www.eclipse.org/downloads/download.php?file=/technology/epf/composer/r...
- http://www.eclipse.org/downloads/download.php?file=/technology/epf/OpenUP/lib...
- http://www.eclipse.org/downloads/download.php?file=/technology/epf/OpenUP/pub...
- http://www.eclipse.org/downloads/download.php?file=/technology/epf/OpenUP/pub...
- http://www.eclipse.org/downloads/download.php?file=/technology/epf/OpenUP/pub...
- http://www.eclipsecon.org/2007/index.php?page=sub/&id=3621
- http://www.embedded-computing.com/departments/eclipse/2006/07/
- http://www-128.ibm.com/developerworks/rational/library/05/1011_kroll/
- C:\Downloads\EPF_Practices_published-0.1-20080606\Publish
Khuyen mai the 1 so link ve Eclipse nua ne
- http://www-128.ibm.com/developerworks/rational/library/05/1011_kroll/
- http://www.eclipse.org/tptp/home/documents/process/development/static_analysi...
- http://eclipsetutorial.forge.os4os.org/in2.htm
OK, any question, ask me ![]()
Jun 21, 2008
How to setup GCS Global Mail with iPhone
Host Name: mail.globalcybersoft.com
User Name: xxx@globalcybersoft.com
Password: xxx
Outgoing Mail Server
Host Name: mail.globalcybersoft.com
Port: 25
User Name: xxx@globalcybersoft.com
Password: xxx
Use SSL: OFF
Jun 7, 2008
How to disable autocorrect function in iPhone
If you have used the iPhone, you'll see the autocorrect/predict text function is very annoyned (for VNese text)
To disable this,
Edit the file /Applications/Preferences.app/Keyboard.plist and add following line
<dict>
<key>cell</key>
<string>PSSwitchCell</string>
<key>default</key>
<integer>0</integer>
<key>defaults</key>
<string>com.apple.Preferences</string>
<key>key</key>
<string>KeyboardAutocorrection</string>
<key>label</key>
<string>Enable Autocorrection</string>
</dict>
The Keyboard.plist is in binary format, you need to convert it into XML and then edit and then convert it back to binary format. Use the following URL for doing such conversion
- Online: http://iappcat.com/plist/bin2xml
- Offline (need to have PERL): http://scw.us/iPhone/plutil
After all, go to the Keyboard setting and turn off the Autocorrect function.
For iPhone 2.0, you basically rename whatever dictionary file you want to disable the autocorrect function for:
- start Mobile Terminal (or use SSH)
- become root using
su(the password is alpine) cd /System/Library/TextInput/mv TextInput_en.bundle TextInput_en_bak.bundle(for English)- The autocorrect feature for English should now be disabled
Have fun
Jun 5, 2008
Link for technologies (1)
It's so hard, so many things to do, i'm so tired, i use this blog to hold my thinking right now, since my PC cannot store it any more...(RAM limited)
- http://softwarecommunity.intel.com/Wiki/GlossaryofTechnicalTerms/803.htm I'm look at this link, and I think that I must build up the Parallel Computing for Global CyberSoft, I have before, but it doesn't make sense, now it's time for Parallel Programming, maybe later...when I'm free.
- http://www.cio.com/article/378115/Outsourcing_._Workable_Business_Models_for_... The Web 2.0 is growing up, is there anything new with Outsourcing 2.0, let look at this later
- The following links are not work, maybe it'll be available later
- I'm looking for a place to download this book http://www.packtpub.com/uml/book/mid/210906cvzwmp#indetail
- LiquiBase, it's so cool, I'm thinking a way to make it works with CI and GCS http://www.liquibase.org/
- Some tips for Eclipse, because I want to apply eclipse at GCS (in replacement of VS) - http://www.eclipse.org/resources/
- How to debug using eclipse - http://eclipse.dzone.com/news/tips-and-tricks-debugging-ecli
- UML with eclipse, I'm thinking about MDA - http://www.eclipse.org/articles/article.php?file=Article-Defining-Generics-wi...
- Mylyn, currently i'm looking for an integration solution to link Bug, Task, Project, Wiki - http://www.ibm.com/developerworks/java/library/j-mylyn1/index.html?ca=dgr-jw2...
- Mylyn again - http://www.ibm.com/developerworks/java/library/j-mylyn2/?ca=dgr-jw22jvmylynp1...
- Refactory eclipse??! - http://www.eclipse.org/articles/article.php?file=Article-Unleashing-the-Power...
- Migrate VC++ to Eclipse CDT, so cool - http://www-128.ibm.com/developerworks/library/os-ecl-vscdt/index.html?ca=dgr-...
- IRStats, some link with Trac - http://trac.eprints.org/projects/irstats
- Trac Installation - http://trac.edgewall.org/wiki/TracOnWindows
- Trac Installation again - http://wiki.forum.nokia.com/index.php/Trac_installation_guide
- TFS, maybe later, but nothing impress in my mind - http://www.codeplex.com/TFSCodeReviewFlow
- Trac and Remote Repository - http://trac.edgewall.org/wiki/TracFaq#can-i-use-trac-with-a-remote-subversion...
- Some useful link for Java CI - http://java-source.net/open-source/code-analyzers
- QJPro - CI again - http://qjpro.sourceforge.net/ant.html
- SVK a solution for SVN mirroring (maybe i'll need later but now) - http://svk.elixus.org/view/InstallingSVK
- It does not work, I don't know what is this, but maybe useful - http://www.mobileinnovation.co.uk/developer_tools/codeScanner/index.aspx
- SVN sync another solution for SVN mirroring - http://svn.collab.net/repos/svn/trunk/notes/svnsync.txt
- SVN sync again http://blog.codefront.net/2007/03/31/setting-up-svnsync-ed-mirrored-svn-repos...
- SVK - http://svk.bestpractical.com/view/SVKTutorial
- Evolution, i'm looking at this when finding a replacement for Outlook - http://download.go-oo.org/evo/
- UIMA - Unstructured Information Management Architecture SDK ???! what is this? - http://www.alphaworks.ibm.com/tech/uima
- Apache UIMA (supporting components for analysing unstructured content such as text, audio and video. )- http://incubator.apache.org/uima/
- Text Analytics Tools - http://www.alphaworks.ibm.com/tech/lrw maybe good for a centralize solution that support our Translators
- Visual Performance Analyzer - http://www.alphaworks.ibm.com/tech/vpa good to see if it works with CI
- JET - the title is so interesting: Create more -- better -- code in Eclipse with JET, http://www-128.ibm.com/developerworks/library/os-ecl-jet/index.html, maybe I'll need some days with Eclispe solution in my mind.
- Eclipse TPTP, i'm currently learn this but don't have time - http://www-128.ibm.com/developerworks/edu/os-dw-os-ecl-tptp-i.html
- Some recommended eclipse reading list - http://www-128.ibm.com/developerworks/opensource/library/os-ecl-read/
- UCM - automating the build/deploy web application - http://www-128.ibm.com/developerworks/rational/library/jun06/tao/index.html
- Some information for working in Flat World environment - http://www-128.ibm.com/developerworks/rational/library/jun06/pollice/index.html
- Software Requirements Memory Jogger - a book, I should find it http://www-128.ibm.com/developerworks/rational/library/jun06/reader/pollice2....
- Agile SCM, what is this?! - http://www-128.ibm.com/developerworks/rational/library/jun06/lee/index.html
- Technical Library for Java - http://www.ibm.com/developerworks/views/java/libraryview.jsp?end_no=200&lcl_s...
- This was found out when I'm looking for a training solution provided for IBM Business Partner, since Global CyberSoft is an IBM Business Partner -
- An example of Bug <> SVN integration http://bugzilla.mkgnu.net/show_bug.cgi?id=417
- ScmBug - http://www.mkgnu.net/?q=scmbug
- ScmBug again - http://files.mkgnu.net/files/scmbug/doc/latest_manual/html-single/manual.html...
- Subversion Wiki - http://www.orcaware.com/svn/wiki/Main_Page
- SVN-Bugzilla - http://www.subversionary.org/projects/svn-bugzilla
- Bug - SVN - Wiki - http://oss.segetech.com/bugz-svn-wiki/
- ScmBug again - http://freshmeat.net/projects/scmbug/
- ScmBug introduction - http://blog.platinumsolutions.com/node/102
- Some useful URL for Subversion - http://subversion.tigris.org/links.html
- ALF - http://www.eclipse.org/alf/alfabout.php this was found out when i'm searching for Application Lifecycle Tools
That's all, Hope I have time to look again this list and find out what is the needed most.
Or if you see something interesting, please drop me a comment.
Apr 27, 2008
Get iPhone Filesystem via SSH
The following code snippet shows you how to get the iphone filesystem via SSH. The file system will be put at /usr/local/share/iphone-filesystem
mkdir -p /usr/local/share/iphone-filesystem |
Apr 15, 2008
Software Domain for Career Development - Business Software
In this post, I'm going to show the roadmap, for involving into Business Software development.
As in Business Software domain, there may have many way for you to go, such as an ERP system, HRM system, CRM system, the system here is mostly to support the business process in an Enterprise.
Some hot applications today can be listed out here are
- SAP: this is an all in one business solution for ERP includes Finance, Human Resource, Project Management, Training, Employee Portal...
- SharePoint: this is an enterprise portal developed by Microsoft and its provide many functionalities such as Enterprise Portal, Document Management, Records Center, Content Management System...
- Microsoft Dynamics AX: this is a Business application of Microsoft
- BizTalk: this is a bridge for connecting LOB application developed by Microsoft
- Surgar CRM: an open-source Customer Relationship Management system
- Oracle
The three important applications I think you could focus is SAP, SharePoint, BizTalk
- SAP: to get involve with SAP, you should have some basic knowledge in a specified business domain such as Finance, Human Resource, Projects...If you want to involve into the Basis core of the SAP, you should have following knowledge
- J2EE
- Web Application
- Basic ABAP
- Database such as MSSQL, DB2,...
- OS: Windows Server, Linux
- SharePoint: the SharePoint is rather simpler than SAP, but you should familiar with Microsoft Technologies such as
- .NET 2.0, Web Parts, Workflow
- Web Services
- Microsoft SQL Server
- Some SharePoint techs: Sites, Lists, Contents...
- Excel Services
- Forms Server
- Microsoft SQL Server Reporting Services
- Windows Server
- BizTalk: this is a integration solution from Microsoft, allows you to integrate your LOBs together. You should know
- Database techs: MSSQL, DB2, Oracle...
- Web Services
- .NET 2.0
- Workflow
Software Domain for Career Development
- Business software: this type of software is related to business domain such as accounting, docketing, ERP, CRM..., for who want to write management application such as ERP, Human Resource Management.
- Analytics: related to data mining, data processing, decision support system. This domain is for who want to dig more in Database, Data Mining, and AI
- Airline reservations: this related to Air Port and the system to manage airline reservation. For who loves Communication + Web + Database
- Banking: related to banking system such as Credit Card, ATM, Online Banking. Those who is interested in banking related system, and should have the secure software mindset
- Commerce: some examples are Trade, Auctions, Bar code scanner. For those who is interested in E-Commerce technology
- Compilers: Dig through the compiler such as Parser, Generation, Linker, Loader
- Communication: some such as e-mail, IM, VOIP, Contact Management, suitable for who loves IP technology
- Computer graphics: Animation, Special Effect, Image Editing...
- Cryptography: RSA, DSA, Secure Key...
- Databases
- Embedded systems: Automotive, Telephony, Medical Device Software, Mobile
- Engineering: Computer Aid Design, Electronic Design Automation, Simulation
- File: related to file such as File sharing, File synchronization, FTP
- Finance: Stock market
- Games
- Information systems: System to manage information such as Personnel Data,
- Logistics: Supply Chain Management, related to Factory Automation
- Manufacturing: CAM
- Music
- Network Management
- Networks and Internet: some related to DNS, Protocols, Router.
- Office suites: Word, Spreadsheet, Presentation
- Operating systems
- Robotics
- Signal processing: Image Processing, Speech Processing, Text Recognition
- Simulation
- Sciences
- Traffic Control
- Training
- Visualization
- Voting
- World wide web: Web Browser, Web Server
- Healthcare
So which domain you would like to join?
Missed something? Fix me.
Apr 1, 2008
Global CyberSoft PM Forum 2008
If you have chance to join the forum, it's so interesting. Here, we share our knowledge and experiences on project management, in order to develop ourself. This year, we have done many things to improve Global CyberSoft. And the year 2008 should be so :-)
Here are some pictures
All people who has attended the seminar

Mr. An Cao

Mr. Vien Nguyen

Mr. Vu Tran

Mr. Quynh Nguyen

Mr. Toan Ngo

Our CEO, mr. Chi Ngo

See you on 2009 PM Forum :-)
Mar 4, 2008
Global CyberSoft Japan blog
Finally anh Dong has created a blog for Global CyberSoft Japan. See it here http://gcsjp.blogspot.com/
Feb 19, 2008
Blogs and Global CyberSoft?
Chúng ta đã chứng kiến sự phát triển rầm rộ của những công ty chuyên về blog như Yahoo (Y! 360), Google (Blogger), Microsoft (Live)…chúng ta cũng đã thấy được sự phát triển của blog trong môi trường doanh nghiệp như là Microsoft, IBM, Sun đã làm…
Blog phần nào đó giúp ích cho sự phát triển của doanh nghiệp
Blogs giúpcho
- Nâng cao hiệu năng làm việc nhóm, thông tin đến 1 cách real-time
- Nâng cao khả năng sáng tạo và ý tưởng mới
- Giúp cho việc chia sẽ kiến thức trong công ty
- Marketing & PR
- Chia sẽ chiến lược của công ty tới anh em
- Kênh thông tin của anh em
- và rất là nhiều nữa
Như ta đã thấy
- and why not http://blogs.cybersoft-vn.com

Ideas and comments are welcome.
Feb 18, 2008
iPhone Jailbreak (1.1.1 & 1.1.2)
Firmware 1.1.1
- Slide the slider to the right to execute the Emergency Calling
- Dial *#307# and select Call. iPhone will display a receiving call, clear the entered number using the X button (in the top right) and the press 0, and Call button. iPhone will receive a call number 1, select Answer, Hold, and then Decline.
- Now you are in the Keypad of the iPhone, select Contact to see All Contact screen.
- In the All Contact screen, press + (on the top-right) to Add contact. In the box First Last, enter what ever you want for the name of the contact. Select the box Add new URL and enter prefs: for the URL, Save and then select Add new URL again to enter new url, this time, enter http://jailbreakme.com and the Save the contact.
- Then in the contact screen, select the prefs: to go into the Settings of iPhone.
- Select General -> Auto-Lock -> Never
- Then back to the Settings creen, select Wifi to connect Wifi for the iPhone. After all, press the Home button to exit.
- Now you are in the Activate iPhone screen, move the slide to go into Emergency Call, press 0 -> Call, Answer, Hold, Decline.
- Select the contact and click on the url http://jailbreakme.com to open jailbreakme.com website, scroll down to the end of the page, select Install AppSnapp?
- You will be back to Activate iPhone, use the Emergency Call to go back into the Contact screen of iPhone, if you see the downloading progress bar, you are successfully. BTW, wait for a minute to download the AppSnapp?. If not, try again until success. After all, the iPhone will automaticall restart and now you are at the Springboard of the iPhone.
- Your iPhone has been unlock with Firmware 1.1.1
Firmware 1.1.2
In summary we will go through following step- Downgrade to 1.1.1
- Jailbreak 1.1.1
- Upgrade to 1.1.2
- Jailbreak 1.1.2
Prerequisite
- Wireless network
- Java: http://www.java.com/en/download/index.jsp
- iTunes: http://www.apple.com/itunes/download/
- iBrickr0.9: http://ibrickr.com/downloads/ibrickr_v0.91.zip
- Jaibreak 1.1.2: http://conceitedsoftware.com/iphone/1.1.2-jailbreak.zip
- iPhone Firmware 1.1.1: http://appldnld.apple.com.edgesuite.net/content.info.apple.com/iPhone/061-3883.20070927.In76t/iPhone1,1_1.1.1_3A109a_Restore.ipsw
- iPhone Firmware 1.1.2: http://appldnld.apple.com.edgesuite.net/content.info.apple.com/iPhone/061-4037.20071107.5Bghn/iPhone1,1_1.1.2_3B48b_Restore.ipsw
Downgrade to Firmware 1.1.1
- Connect the iPhone with PC, hold the Power (the top right button) and Home (central button) at the same time until the iPhone screen turn off, continue holding those button until the iPhone screen turn on and then release the Power button but continue holding Home button until iTunes recognize the iPhone is in the Recovery Mode.
- Hold Shift and click into the Restore button in iTunes, and then select the Firmware 1.1.1 which you have downloaded before. Wait until iTunes restore the iPhone and then it display the error messsage like 'Error 1015', click OK and then another message is displayed, keep click OK. After all, turn off iTunes but still plug the cable in.
- Open Task Manager and end the process iTunesHelper.exe
- Unzip iBrickrs0.9 which you have downloaded before and execute the iBrickr.exe. Select Boot the Phone in the iBrickr window. At this time, the iPhone screen will display in red color, leave it alone and then the iPhone will reboot. This time, iPhone will display the Activate screen, turn off iBrickr and un-plug the cable.
- Your iPhone has been downgraded to Firmware 1.1.1
Jailbreak Firmware 1.1.1
Follow the step at Firmware 1.1.1
Upgrade to Firmware 1.1.2
- After Jailbreak firmware 1.1.1, on the Springboard of iPhone select Installer, select tab Install, select Tweak (1.1.1) -> Oktogrep and press Install to install it. After the installation finished, press OK button, press Home button to exit the Installer and wait for about 10 seconds. Restart your iPhone by press and hold the Power button and then move the Slider to turn off. Restart iPhone, connect the iPhone with PC and execute iTunes
- On iTunes, after it recognized iPhone, hold Shift and click the Update button, select the Firmware 1.1.2 which you have downloaded before to update. After the Update finished, close iTunes and unplug the cable from the PC and then re-plug the cable to the PC.
- Your iPhone has been upgraded to Firmware 1.1.2
Jailbreak 1.1.2
- Unzip the Jailbreak 1.1.2, and execute the windows.bat (you must have Java installed). The 1.1.2 Jailbreak window appears, check the Install SSH, and enter root password is alpine. Then click the Jailbreak button. After the jailbreak finished, your iPhone will automatically reboot and you can get into the Springboard of iPhone.
- Your iPhone has been jailbreak with firmware 1.1.2 but without Phone and SMS function.
Feb 17, 2008
Meet Charlie - what is Enterprise2.0?
Meet Charlie - what is Enterprise2.0?
From: slgavin, 9 months ago
A visual and entertaining example of web2.0 within the corporation.
Visually inspired by the brilliant Meet Henry by Cheree Moore of Ethos3 Communications! Check it out: http://www.slideshare.net/chereemoore/meet-henry
SlideShare Link
Feb 16, 2008
RSS for Global CyberSoft

Hey, have you heard about Yahoo! Pipes?
From: http://pipes.yahoo.com
About Pipes
Pipes is a powerful composition tool to aggregate, manipulate, and mashup content from around the web.
Like Unix pipes, simple commands can be combined together to create output that meets your needs. Here are a few popular ways the service can be used:
- create your ultimate custom feed by combining many feeds into one, then sorting, filtering and translating them.
- geocode your favorite feeds and browse the items on an interactive map.
- remix your favorite data sources and use the Pipe to power a new application.
- build custom vertical search pages that are impossible with ordinary search engines.
- power widgets/badges on your web site.
- consume the output of any Pipe in RSS, JSON, KML, and other formats.
To learn more about Pipes, and how you can use it, visit the Pipes Documentation.
Sound great?
Finally I have tried to build up a pipe for Global CyberSoft, it's very cool and easy, in just a minute you can have your own feeds ![]()
Try it here: http://pipes.yahoo.com/pipes/pipe.info?_id=a7d8303c036a025a1a6a447ffebb3f39
Enterprise 2.0: Five Innovations the CIO Shouldn’t Miss
- "Blogs Away" with new communication techniques – more CXOs are taking advantage of this important Web 2.0 innovation.
- Social Networking – It's not just for kids! – At the core are software from Google (like AJAZ and Google Mashup Editor) and Microsoft products (like Popfly and Silverlight).
- Unified communications – Microsoft Office Communication Server and Cisco's Unified IP phones are leading the charge.
- A rolling MOSS gathers no stones- MOSS can be views as either a challenge to manage for IT shops or an important innovation catalyst for business processes.
- AAA: Anytime, Anywhere, Anybody – there is no place to hide, unless you press the Off button.
Read the entire article by Jack Santos on CIO here.
Feb 14, 2008
Create a Dashboard in iPhone
You have seen the dashboard in iPhone UI or in Mac OS X UI. The following code snippet shows you how to create a dashboard in iPhone native application.
The code is Object C format
- (UIButtonBar *)createButtonBar
{
UIButtonBar *myButtonBar;
myButtonBar = [[UIButtonBar alloc]
initInView: self
withFrame: CGRectMake(10.0f, 380.0f, 300.0f, 100.0f)
withItemList: [self buttonBarItemList]];
[myButtonBar setDelegate: self];
// This set the style of the bar
[myButtonBar setBarStyle: 3];
// This set the tracking mode (effect when clicking on the button of the bar)
[myButtonBar setButtonBarTrackingMode: 1];
int buttons[3] = { 1, 2, 3 };
[myButtonBar registerButtonGroup: 0 withButtons: buttons withCount: 3];
[myButtonBar showButtonGroup: 0 withDuration: 0.0];
/* This set the layout of the button */
int tag;
for (tag = 1; tag < 4; tag++)
{
[[myButtonBar viewWithTag: tag]
setFrame: CGRectMake(10.0f + ((tag-1)*(80.0 + 10.0)), 1.0f, 100.0f, 80.0f)
];
}
return myButtonBar;
}
The item list of the button bar
- (NSArray *)buttonBarItemList
{
return [NSArray arrayWithObjects:
[NSDictionary dictionaryWithObjectsAndKeys:
@"buttonBarClicked:", kUIButtonBarButtonAction,
@"button_back.png", kUIButtonBarButtonInfo,
@"button_back_pressed.png", kUIButtonBarButtonSelectedInfo,
[NSNumber numberWithInt: 1], kUIButtonBarButtonTag,
self, kUIButtonBarButtonTarget,
@"Page 1", kUIButtonBarButtonType,
@"0", kUIButtonBarButtonType,
nil
],
[NSDictionary dictionaryWithObjectsAndKeys:
@"buttonBarClicked:", kUIButtonBarButtonAction,
@"button_open.png", kUIButtonBarButtonInfo,
@"button_open_pressed.png", kUIButtonBarButtonSelectedInfo,
[NSNumber numberWithInt: 2], kUIButtonBarButtonTag,
self, kUIButtonBarButtonTarget,
@"Page 2", kUIButtonBarButtonType,
@"0", kUIButtonBarButtonType,
nil
],
[NSDictionary dictionaryWithObjectsAndKeys:
@"buttonBarClicked:", kUIButtonBarButtonAction,
@"button_next.png", kUIButtonBarButtonInfo,
@"button_next_pressed.png", kUIButtonBarButtonSelectedInfo,
[NSNumber numberWithInt: 3], kUIButtonBarButtonTag,
self, kUIButtonBarButtonTarget,
@"Page 3", kUIButtonBarButtonType,
@"0", kUIButtonBarButtonType,
nil
],
nil];
}
The click message, which will handle the click event of the button bar
- (void)buttonBarClicked: (id) sender
{
}
And you will got a nice UI like this

That's all, Have fun with iPhone & Object C coding ![]()